ARKM平台前端逆向
1.随便找个包,发现headers中携带X-Payload参数,堆栈点一点,找到加密位置
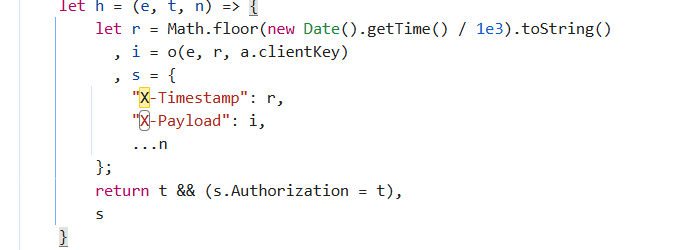
2.控制台打印获取a.ClientKey

3.Python编写加密函数
import requests
import time
import hashlib
import json
query = "bybit"
salt = "gh67j345kl"
def make_payload(path: str, ts: str) -> str:
"""复现 JS 里的两段 sha256 逻辑"""
step1 = hashlib.sha256(f"{path}:{ts}:{salt}".encode()).hexdigest()
return hashlib.sha256(f"{salt}:{step1}".encode()).hexdigest()
path = "/transfers"
ts = str(int(time.time()))
payload = make_payload(path, ts)
# 1. 构造与浏览器一致的请求头
headers = {
"accept": "application/json, text/plain, */*",
"accept-encoding": "gzip, deflate, br, zstd",
"accept-language": "zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6",
"origin": "https://intel.arkm.com",
"referer": "https://intel.arkm.com/",
"sec-ch-ua": '"Chromium";v="142", "Microsoft Edge";v="142", "Not_A Brand";v="99"',
"sec-ch-ua-mobile": "?0",
"sec-ch-ua-platform": '"Windows"',
"sec-fetch-dest": "empty",
"sec-fetch-mode": "cors",
"sec-fetch-site": "same-site",
"user-agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 "
"(KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36 Edg/142.0.0.0",
"x-timestamp": ts,
"x-payload": payload,
"cookie": "_ga=GA1.1.1952893755.1763016182; _fbp=fb.1.1763016181936.907337779104231599; _clck=1erlme0%5E2%5Eg0z%5E0%5E2143; mp_db580d24fbe794a9a4765D"
}
# 3. 发起请求
url = f"https://api.arkm.com{path}"
resp = requests.get(url, headers=headers, timeout=10)
print(json.dumps(resp.json(), ensure_ascii=False, indent=2))
4.获取完整的项目方关联地址,参与到后续区块扫描流程
